Helping survivors of domestic violence
A digital security guide for organizations
Tor Project Community Team
Attention
- This material is provided to support organizations and individuals working with gender based violence.
- We're sharing some examples, and you will probably need to contextualize and adjust to your local reality.
- Before following or using this guide, it’s crucial to read it very carefully.
Domestic violence
- Home isn’t a safe space for everyone.
- To seek help or get in touch with a survivor can be risky for both sides.
- We can use privacy technologies like Tor to communicate securely with survivors.
- Digital security tools can help you, but you will also need operational security.
Why do we need anonymity?
- Self-defense: we need to protect ourselves and our solidarity networks.
- Surveillance threats from family, (ex)partners, bad people on the internet.
- The business model of the internet: big data, advertising, non-consensual tracking.
Specific digital threat scenarios
Examples of threats can include someone like a family member or an ex-partner that:
- is harassing the survivor through their cell phone.
- is harassing them through social media.
- is stalking their location.
- is monitoring their online activity.
- has unwanted access to their online accounts.
- is limiting access to the survivor's devices and/or online activities.
Common threats
- Psychological pressure to share survivor passwords or the access to their devices or online accounts.
- Tracking their phone live location using Google, Apple ID ("Find my phone"), or messaging Apps.
- Accessing their online activity, like browser history, social media private messages, email, messages.
New advanced threats
- If you suspect that the survivor is being monitored and need help, please contact an organization close to you.
- Stalkerware is a piece of software that enables someone to monitor your devices and online activities.
- As they're very good at hiding, some stalkerware aren't detected easily by antivirus.
- Coalition Against Stalkerware: https://stopstalkerware.org/
Stalkerware indicators
- Your device goes missing and reappears.
- Strange behavior:
- Apps closing or opening without your intervention.
- Active sessions on Apps that you didn't give authorization.
- If you want to learn more about this topic, we can schedule a specific training about Stalkerware. Please contact us: training@torproject.org.
Security Plan
Your security plan
- Security is a process: it aims to help you keep moving in your life.
- Security is the opposite of paranoia.
- Digital security tools can help you, but we need to take a holistic approach:
- To create a security plan, we will look and understand the unique threats you face and how you can mitigate those threats.
Personal context is important
- Let’s discuss different kinds of scenarios and when it helps to plan about privacy and security.
- Does the abusive person still have access to your devices?
- Do you suspect that they can see your private messages?
- Or maybe the abuser never had access to them?
- Do you depend financially on the abuser?
- Risks and strategies are different.
Exercise - your security plan
Use a blank page to answer these questions:
- What do I want to protect? (assets)
- Who do I want to protect it from? (adversary)
- How likely is it that I will need to protect it? (probability)
- How can I protect it? (mitigation)
Take the context into consideration.
Example - a basic security plan
- Assets: We want to protect our digital communications with a survivor from being intercepted, hijacked, or exposed to the aggressor.
- Adversaries: family members, (ex)partner(s), machitrolls.
- Probability: high.
- Mitigation: opsec, strong passwords, device encryption, 2 factor authentication, ephemeral communication.
Good practices
- Keep your Operating System up to date.
- Do not keep your device (computer, phone) unlocked.
- Do not plug random USB devices into your computer.
- Do not download any files or click on any links sent to you from unknown sources or the aggressor.
Good practices
- Avoid prying eyes and shoulder surfing.
- Do not “doxx” yourself: be careful not to disclose publicly aggregated information about yourself, e.g., your full name, ID picture, home location, and other personal information.
- Search for safe ways to report the aggressor. You can use Tor Browser to find contacts for domestic violence hotlines and organizations.
Good practices: Two Factor Auth (2FA)
- Enable Two Factor Authentication (2FA) in your social media accounts and email. Nobody can log in without the 2 factor authentication code.
- Apps: andOTP, Tofu Authenticator, and Google Auth.
- Check this list of websites that support 2FA: https://2fa.directory/
Getting help
- Security is not always an option.
- If someone else forces you to share your password, or demands to look through your phone, that is abuse and it's not your fault.
- There’s no shame to ask for help. Sometimes others are in a better position to help us.
Anonymous browsing
What is anonymous browsing?
- Anonymous browsing does not trace you and does not track you online.
- If you need to report something anonymously, you can use Tor Browser to do so.
- Tor Browser hides your location, erase your browser history and you leave no trace while navigating online.
- You do not need administrative permission to install Tor Browser.
- You can delete Tor Browser after using it. Just remember to empty the trash.
What is Tor?
- Free software and an open network
- Mitigates against surveillance and censorship
- Run by a US non-profit and volunteers from all over the world
- It’s Tor, not TOR
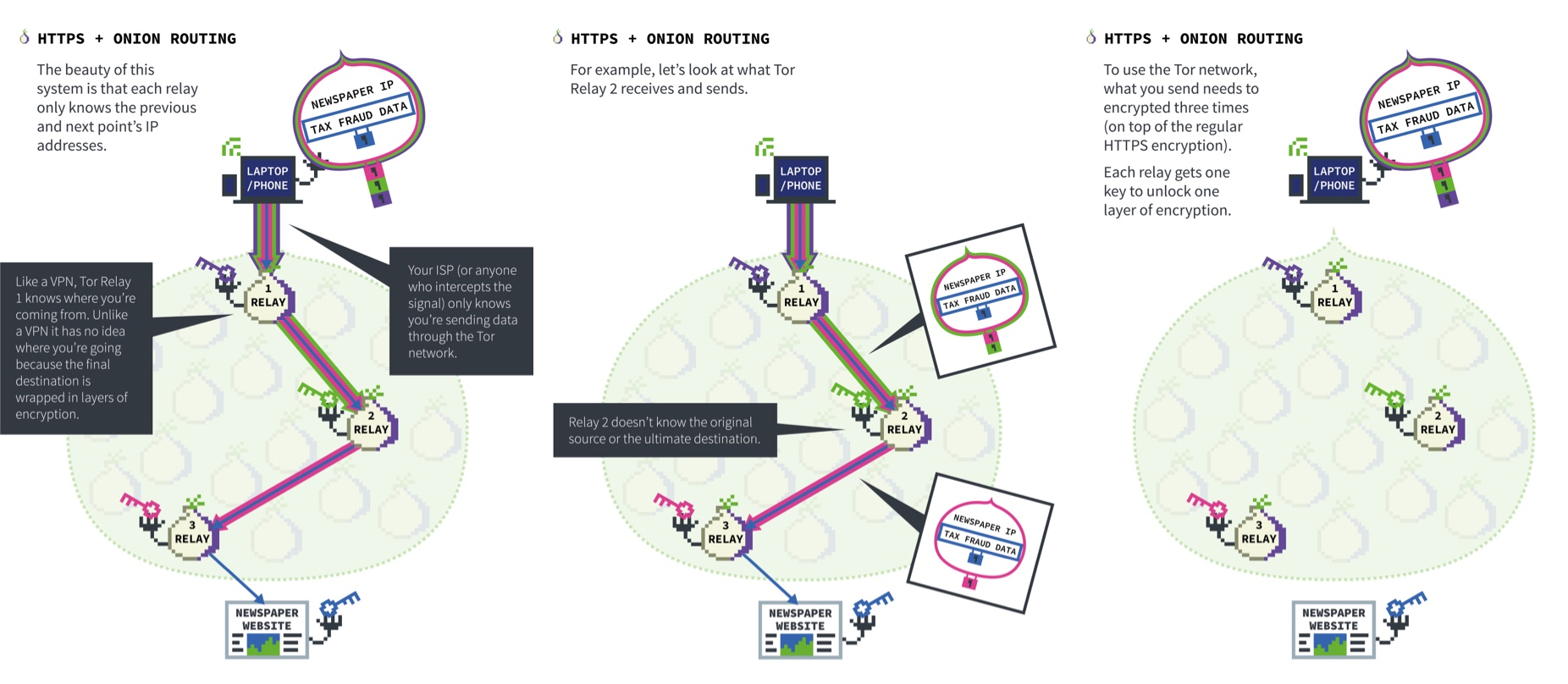
How Tor relays work
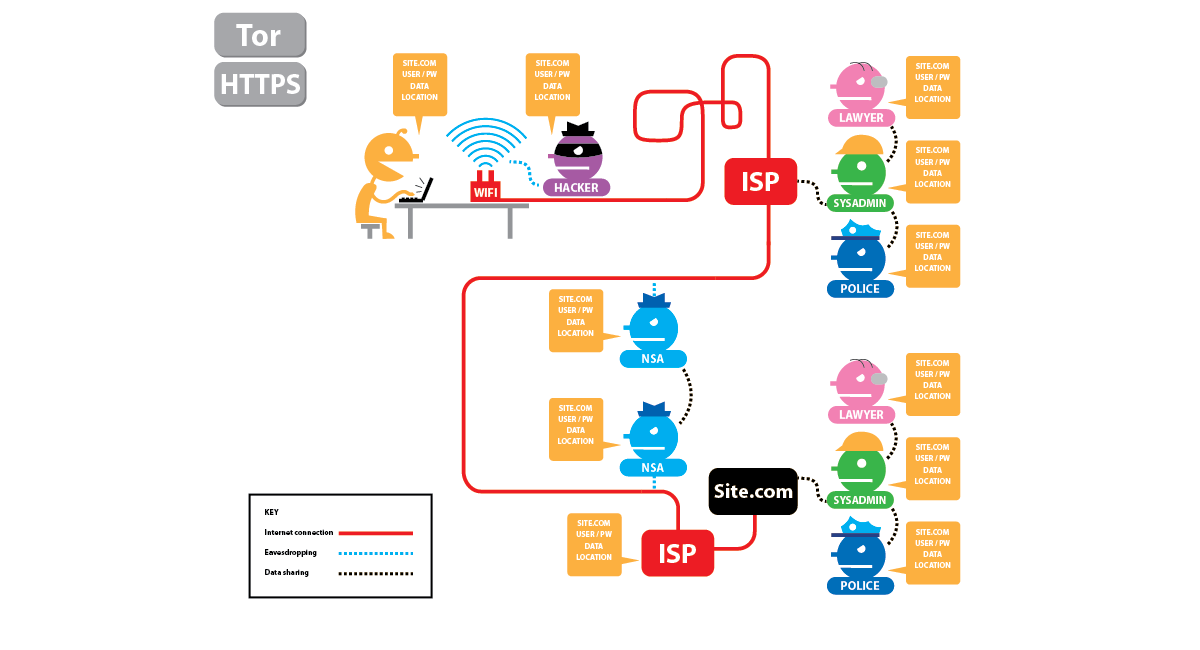
Who can see your activity without Tor or HTTPS?
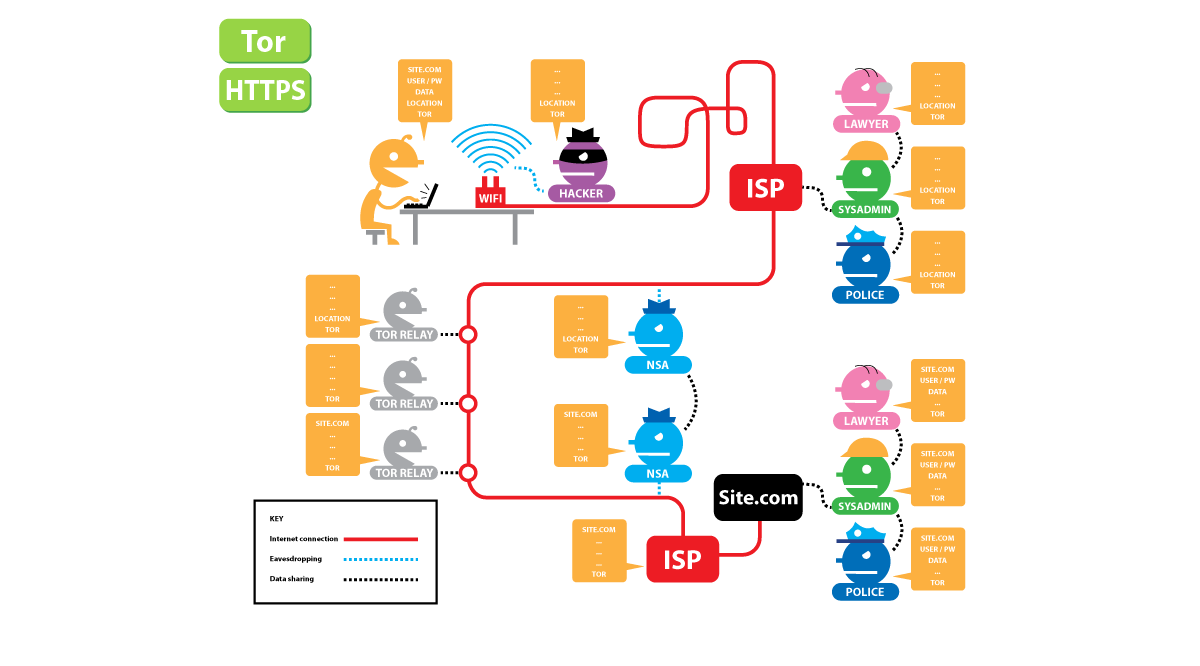
Who can see your activity with Tor and HTTPS?
Tor Browser
- little-t tor + patched Firefox.
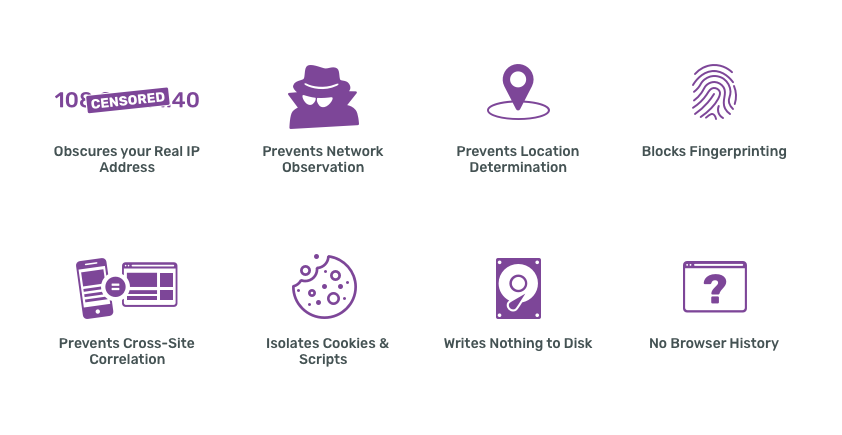
- Spies can’t see the websites you visit.
- Websites can’t track you or see the other sites you visit.
- Prevents other privacy violations like fingerprinting or 3rd party cookies.
- Writes nearly nothing to disk.
- There is no browser history.
- Cross platform: Windows, macOS, Linux and Android.
Tor Browser Features
Tor Browser
Using Tor Browser for Android
- Find it in Google Play or F-Droid.
- You don’t need to install Orbot.
Onion Browser
- Tor Browser for iOS.
- Find it in the app store.
- Lots of fake Tor Browsers in the iOS store.
- Very rudimentary.
- Crashes on sleep.
Ephemeral communications
Ephemeral communication
- In some cases, we need to communicate in a way that leaves almost no persistent traces.
- Regular communications channels like phone calls and messaging Apps leave a lot of metadata.
- Using tools like OnionShare and Tor Browser, you will have an ephemeral communication: no metadata nor browsing history.
OnionShare chat rooms
- Using OnionShare you can create anonymous and temporary chat rooms to communicate in a secure way. After you close Tor Browser, there will be no trace on the computer.
- Survivors or organizations can contact you anonymously to protect their identity.
- Sharing the chat room link using an encrypted messenger app is a good practice.
OnionShare chat rooms
After installing OnionShare, Click “Start Chatting” and then “Start chat server”.
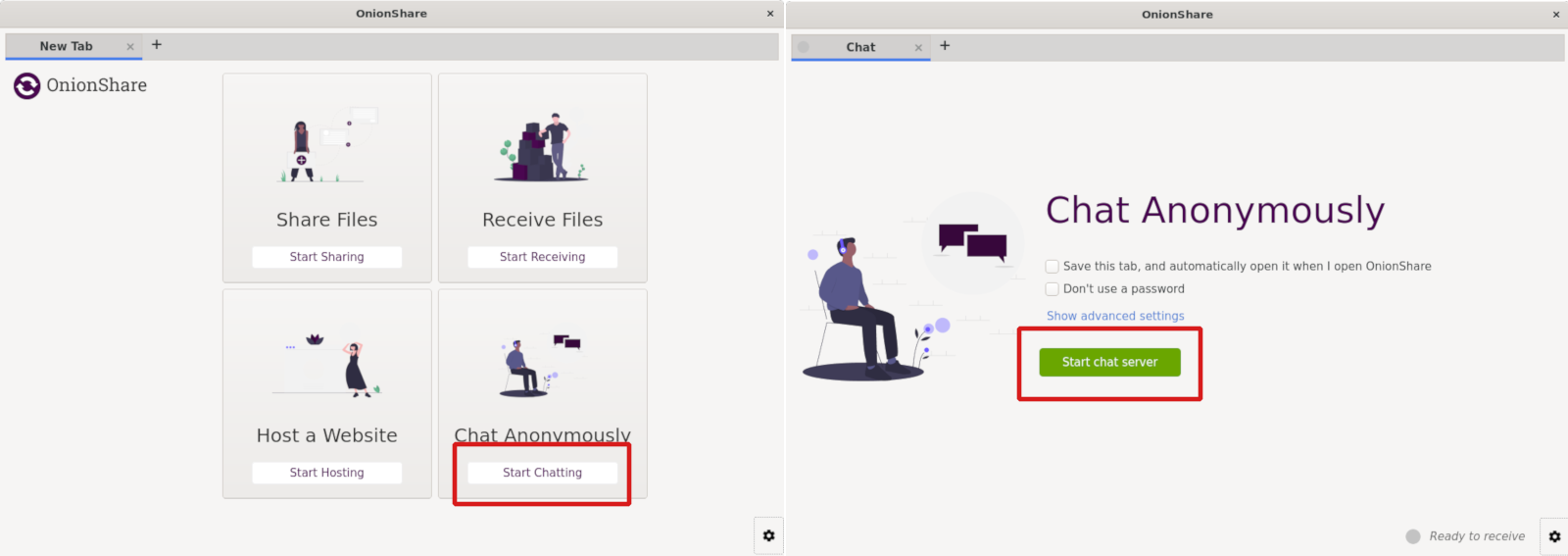
OnionShare chat rooms
Copy and share the chat room link with your contact.
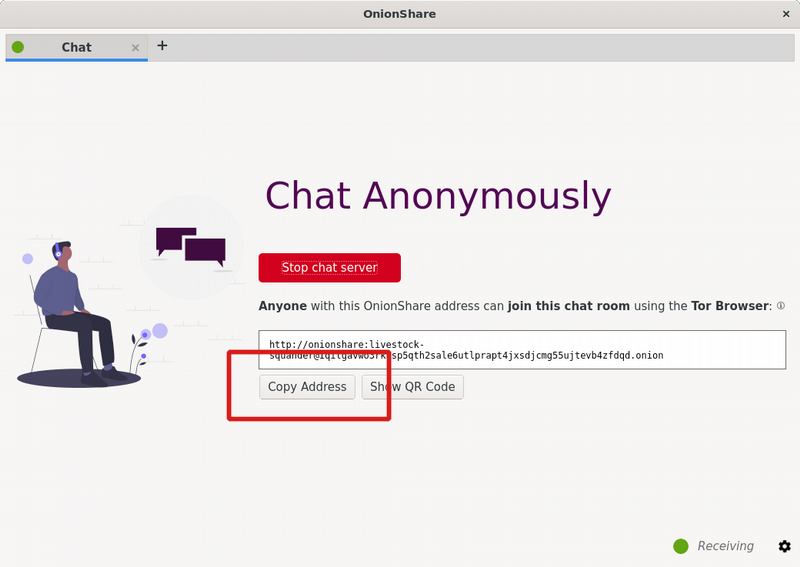
OnionShare chat rooms
Open the link on Tor Browser. Your contacts only need Tor Browser to access the chat room.
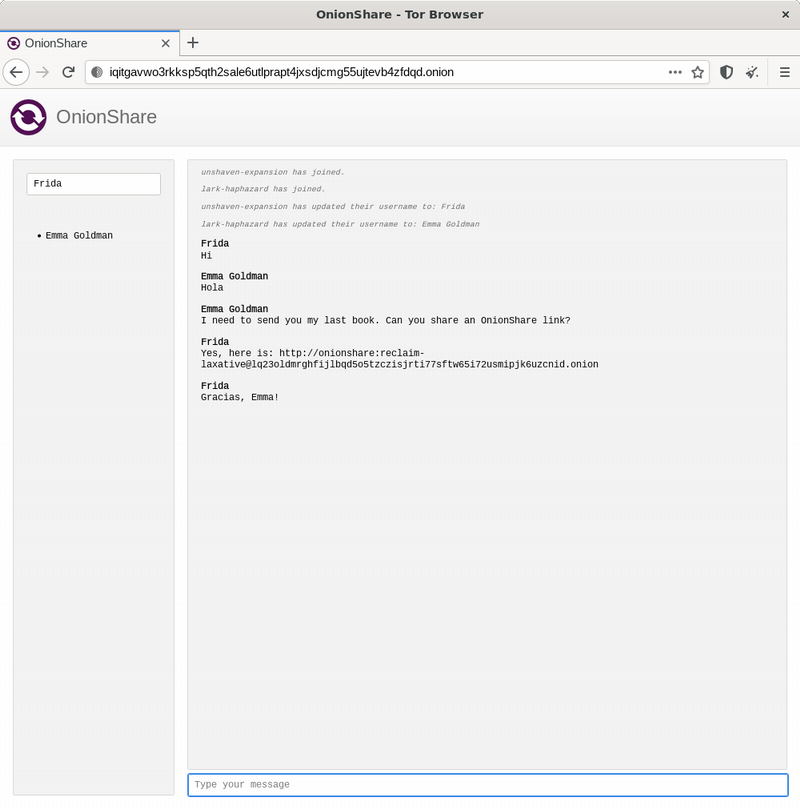
File sharing with OnionShare
- Anyone using Tor Browser can send/upload anonymously evidence of abuse to an organization.
- An organization can set up OnionShare to receive tips and evidence. They can also configure it to share resources anonymously, like Google Drive, but anonymous.
- There are no file size limits and no need to trust third parties like Dropbox or Google Drive.
File sharing with OnionShare
- Once the file is added, click "start sharing".
- Tip: To allow downloading more than once, e.g. for your group, uncheck the first box.
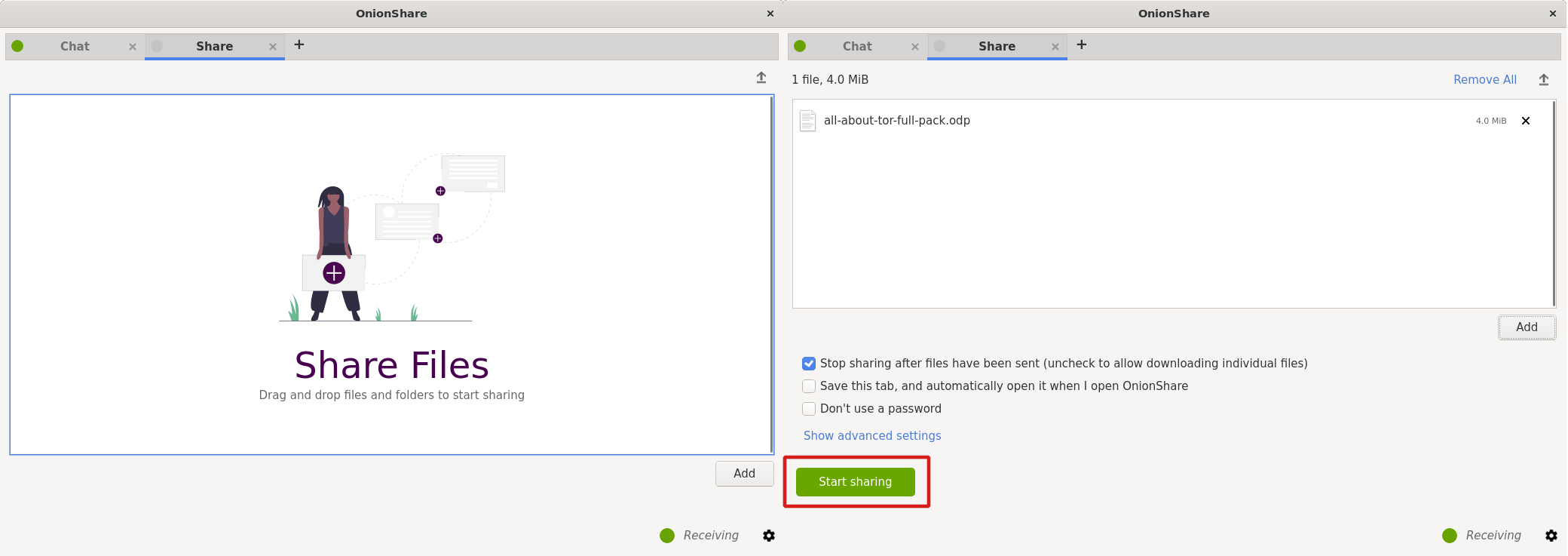
File sharing with OnionShare
Copy and share the address with your contacts (e.g. chat room, Signal group).
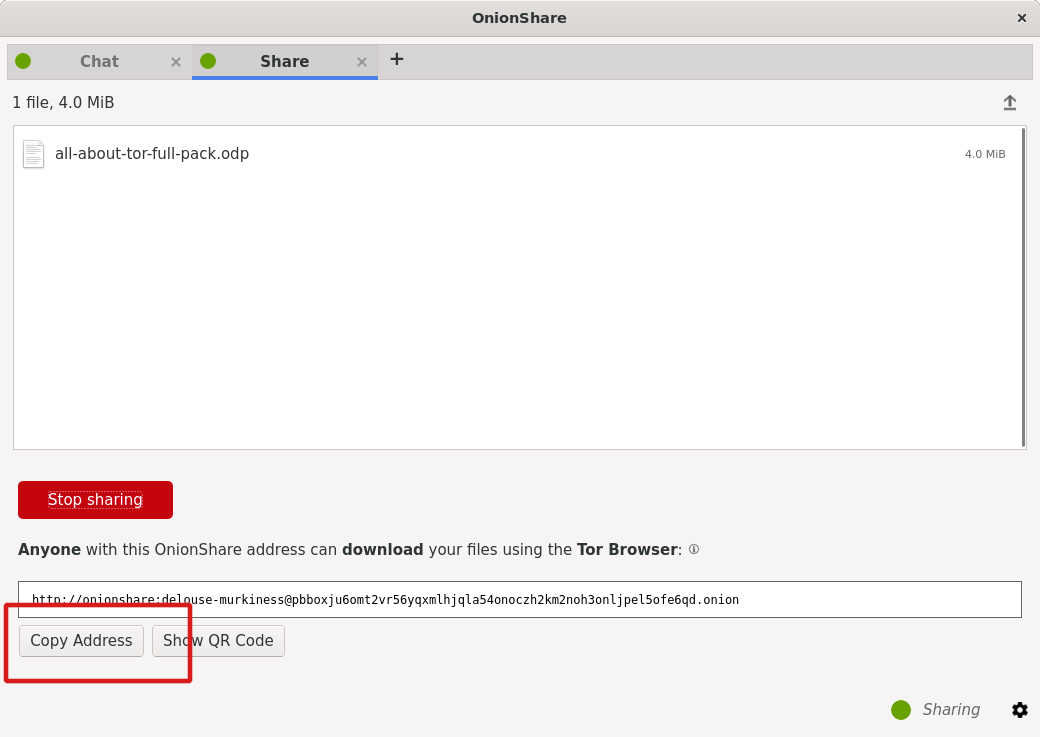
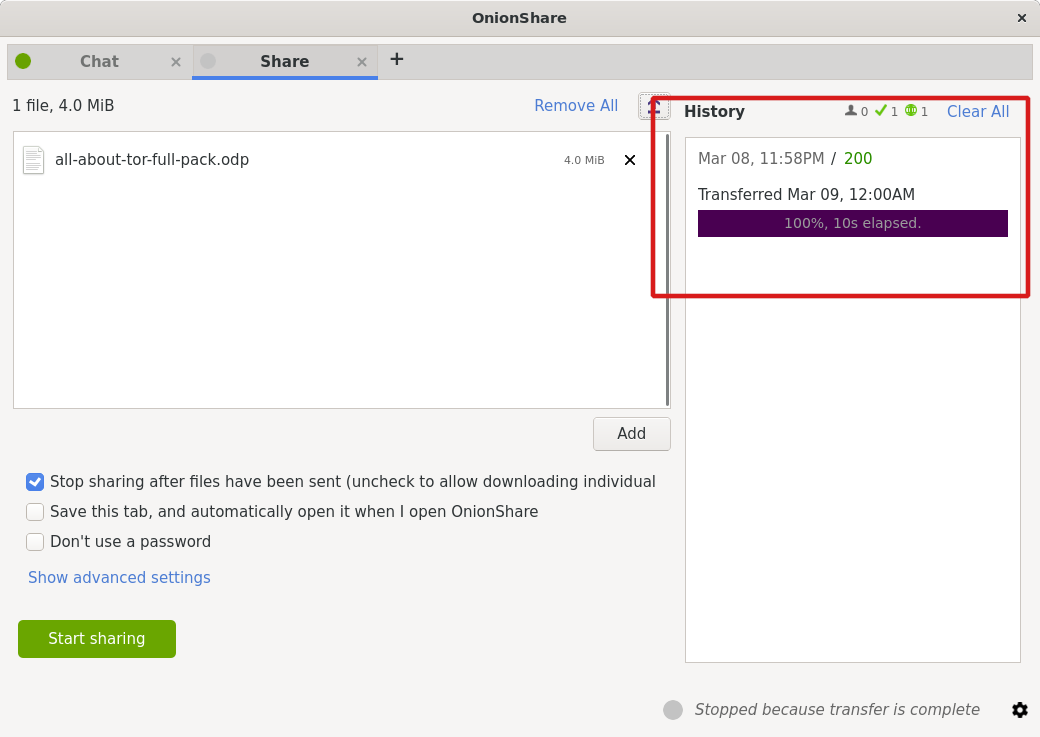
File sharing with OnionShare
When they finish downloading, you will see a notification alert in OnionShare’s history.
More references
- Tor Support – https://support.torproject.org/
- Tor Browser Manual – https://tb-manual.torproject.org/
- Safety Net Project - https://www.techsafety.org/
- Take Back the Tech: https://www.takebackthetech.net/
- Ciberseguras: https://ciberseguras.org/
- Refuge Tech Safety: https://refugetechsafety.org/
More references
- GenderIT: https://www.genderit.org/
- Acoso online: https://acoso.online
- Surveillance Self-Defense: https://ssd.eff.org/en/module/your-security-plan
- Hack Blossom: https://hackblossom.org/domestic-violence/
Thank you!
